Voyager Analytics
Voyager Analytics is a solution to record and replay maritime voyages, and view map with current and past vessel positions and associated analytics. It is enabled by a secure cloud and AI/ML technology for real-time / historical analytics on vessel path, weather, equipment health and environment. It includes real-time warnings of unusual events and anomalies, prescriptive guidance, and GPS spoof detection. The Voyager Analytics IoT device integrates with a vessel’s CAN bus and can gather data independently with optional add-on sensor suite.

WindowsSCOPE - Cyber Forensics Tool
A GUI-based memory forensic capture and analysis toolkit. Allows for the import of standard WinDD memory dumps which are then automatically reverse engineered and presented in an easy-to-view format for forensic analysis in a central location. Applications include digital forensics, memory forensics, cyber crime investigation, cyber defense, cyber attack detection, cyber analysis, and other reverse engineering activities. More Details Rent Now – Cloud Version
Buy node-locked version at WindowsSCOPE Store
MRoT - Mobile Roots of Trust
Mobile Roots-of-Trust (MRoT), which are highly trustworthy tamper evident components, provide a foundation to build security and trust for mobile devices. MRoT, is a fully software-based dynamic mobile trusted module technology, supported by DHS S&T Cyber Security Division (CSD). MRoT measures and verifies the device’s static and runtime state (e.g., boot loader, operating system, apps, etc) to enable trust and security. It can be utilized to detect malicious system change or activity, and to ensure that access to critical information and software can only be performed in a trusted state. It requires no modifications to the underlying operating system kernel, nor any manufacturer or service provider support for insertion. It comes with a user interface that allows adding mobile applications to the MRoT protected vault as well as a standard API.
Contact us for pricing

ThreatSCOPE Base - Vulnerability Analysis and Visualization Tool
ThreatSCOPE Base is a system assurance tool at the binary level for analyzing software vulnerabilities, cyber threats, and potential paths for exploit. It builds on a new concept that is fundamental and does not rely on signatures nor solutions tailored for particular known cyber exploits. Its core technology is patented; some of its components are supported by DARPA, DHS, and Air Force. The tool supports ARM, MIPS, and PowerPC binaries and builds on a sophisticated program analysis framework implementing a new theory of identifying vulnerabilities. The result of the tool is graphical and includes guidance for vulnerability testing. Various metrics are employed to quantify the level of exploitability. Can be used for evaluating vulnerabilities as part of the development process and/or qualifying third-party modules/libraries. ThreatSCOPE customers include leading international manufacturers of automotive embedded systems. In addition to ThreatSCOPE Base, we are also in the process of adding a variety of additional features including support for instrumentation/code-injection as well as modeling. Please contact us for more information regarding these technologies.
Contact us for pricing
UniQore and TrustGUARD Processor Cores - Secure Softcore CPUs for FPGAs
UniQore and TrustGUARD are a family of soft-core secure processors for securing embedded systems with FPGAs or end-points with add-on FPGA cards. They are synthesizable and can be instantiated in FPGA logic. BlueRiSC invented the concept of unique instruction sets and interfaces – made unique to each product line or device depending on customer integration. These two secure processor families target different use cases. In particular, UniQore commercial is a very low overhead processor core that can be used as an add-on to a customer reconfigurable hardware. Both come with ecosystem and security firmware as well as standard interfaces for Xilinx, MicroSemi, and Altera FPGAs. They build on unique, patented concepts for securing the internals of a device and/or software against various kinds of attacks.
Contact us for pricing
ImmuneSoft - Software Immune System
ImmuneSoft, is a runtime system for self-healing software in the field that is inserted into a binary. With the emergence of the Internet of Things, consisting of potentially billions of autonomous devices as well as networked embedded systems with limited access, it has become clear that keeping up with patching software vulnerabilities rapidly approaches its limits of feasibility. Built upon a patented theoretical concept and sponsored by both DHS and Darpa, ImmuneSoft is capable of healing itself in the field without apriori knowledge of an attack. The software immune system introduces minimal overhead and has been shown to could have uncovered the Heartbleed security vulnerability, that affected most of the Internet servers. In addition to self-healing (autonomously), it can be used to provide guidance for a quick recovery from an exploit situation, somewhat similar to the incremental automation of self-driving cars, as well as employed as part of security testing. ImmuneSoft customers include leading international manufacturers of automotive embedded systems.
Contact us for pricing
CaptureGUARD ExpressCard - Gateway to Forensics
This is an ExpressCard platform that enables access to locked Windows computers allowing live forensic acquisition/analysis in these otherwise inaccessible systems. Watch this video demonstration of CaptureGUARD Gateway bypassing Windows login passwords at the WindowsSCOPE product site. Other than Windows operating systems can also be quoted.
Buy Now at WindowsSCOPE Store
WindowsSCOPE On-Demand Report
On-demand memory forensic and analysis reporting for a given memory snapshot. Allows for upload of standard WinDD memory dumps which are then automatically reverse engineered and analyzed to create a report. This report is then delivered via email and made available for download on your account page. Applications include digital forensics, memory forensics, cyber crime investigation, cyber defense, cyber attack detection, cyber analysis, etc.
Coming Soon

EPRIVO Private Email Service
EPRIVO is the only private email service that works with your existing email address, and allows you to send private encrypted emails with privacy controls. It does not store emails keeping security and email provider separate. It pioneers physical security, avoiding vulnerabilities with digital security alone. Add industry-unique privacy controls for each sent private email, enabling full sender-control in both cloud and recipients’ devices. Secure emails can be recalled to make them vanish anytime. In addition, any received regular emails from any account can be privatized – archived and encrypted – only in EPRIVO. Available on the app stores on all major platforms (iOS, Android, macOS and Windows).
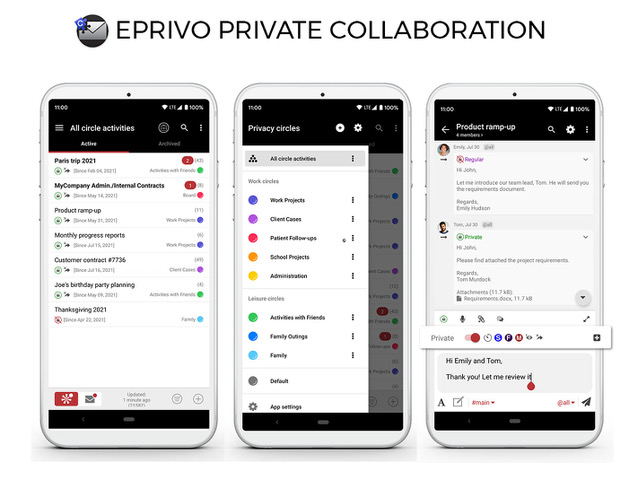
EPRIVO Private Collaboration
EPRIVO Private Collaboration, available on Android & Windows PC is a new paradigm for encrypted private collaboration that tightly integrates with private email – ideal for employees working remotely and consumers. This concept enables a unified view across collaboration and email, while adding privacy controls and encryption. Organize and secure your work and personal interactions with Activities and Privacy Circles. Add members (EPRIVO or non-EPRIVO) to an Activity to collaborate privately via email. Collaboration messages can also be seen as email conversations. Information/resources exchanged can be encrypted and privacy controls added. Recall sent encrypted messages anytime to make them vanish. EPRIVO Private Collaboration service comes with a free trial period – no purchase necessary.
More Details
Download the EPRIVO Private Collaboration app
Pricing

EPRIVO Private Identity Guard
EPRIVO Private Identity Guard, available on iOS (coming soon on Android), is a new privacy concept built to protect your identity when you book travel, purchase something online or sign up for a newsletter. It is based on monitored virtual addresses with cryptographic authentication, privacy enforcement and confidentiality, and associated privacy service. The app locally monitors and alerts you in case of privacy leakage. Easily disable and replace a virtual address anytime in the app. EPRIVO Private Identity Guard comes with a free trial period.
More Details
Download the EPRIVO Private Identity Guard app
Pricing

GPS IntelliSense
The GPS IntelliSense Bolt-on ML/AI Spoof Detection capability provides an independent, data-scalable, and evolving-threat, situational awareness capability with flexible integration options. It is a complete software system to make predictions that is provisioned for integration with GPNTS and GHOST products, as well as others. It supports a variety of attack models. This is a collaboration between BlueRISC and Raytheon Missile and Defense (RMD).
